- 0 Posts
- 33 Comments
I’m not an expert, but it sounds like if you finish a session of valorant, the anti cheat never unloads and continues to monitor memory and files.
Easy Anticheat though, according so some sources, only runs during game play.
Riots Anticheat has a bad history though. But both essentially are black boxes that send details both hash and samples back to their owners for them to approve what’s on it computer. Opened a medical record? It’s probably been hashed and sent back.
Opened your employers accounting files when working from home? details you probably sent riot a copy.
Both can be updated. There’s no guarantees that riot won’t do something nasty against a portion of high value targets. They know you from your payment details. They can identify, update the module and get anything they like, they have root.
Anticheat has a history of being a tool for hackers. https://www.vice.com/en/article/hackers-are-using-anti-cheat-in-genshin-impact-to-ransom-victims/
There’s no upside for the user. Mostly because they don’t work anyway.

Yes but they’re hoping a percentage of people don’t go looking for news that their game has been removed and they need to take action to get a refund.
They remove it from the store automatically, but don’t refund automatically.
Though I bet there may be an argument that the payment platform being Apple means it’s opaque to square, it’s still always customers losing. Even if it’s just a percentage.

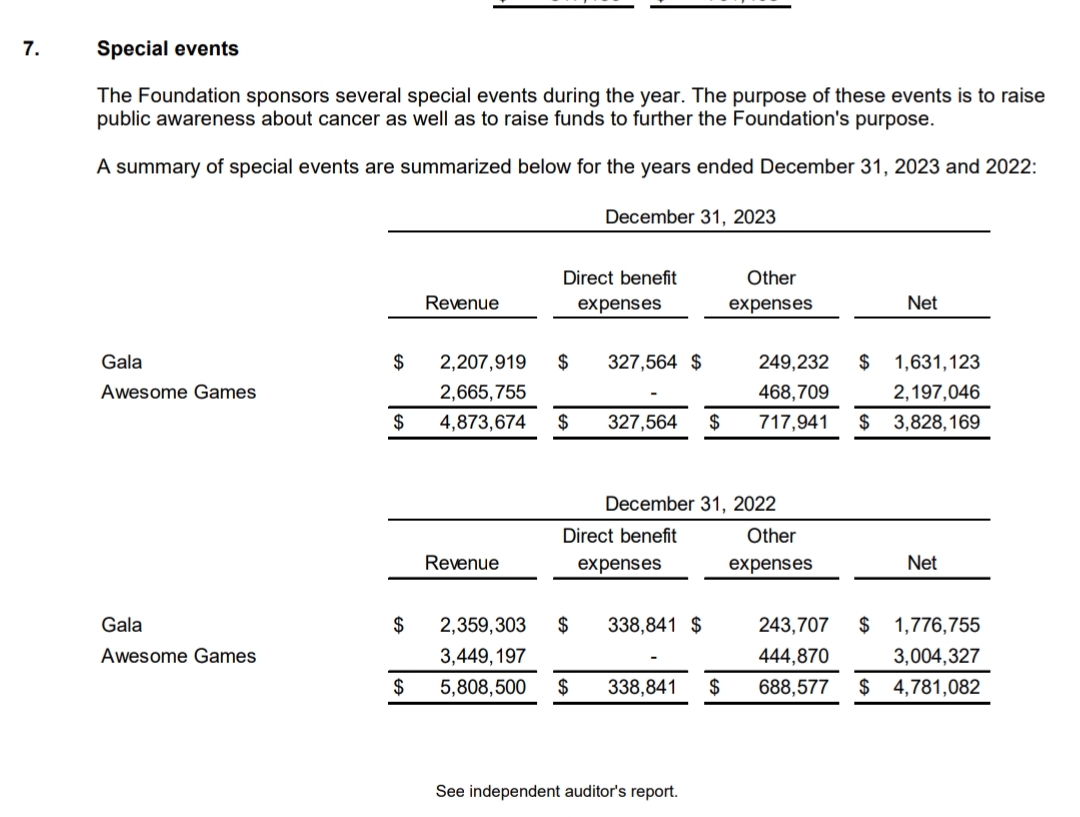
The charity is real, and it took me about 2 minutes to search for their 22-23 audited financial records here https://preventcancer.org/about-us/financials/financial-statements-and-990-forms/
If you go to page 16 you can see the event notes for AGDQ for those two years.
I spent an additional couple of minutes using the propublica lookup. https://projects.propublica.org/nonprofits/organizations/521429544

Steve Gibson’s InControl probably a no research needed option https://www.grctech.com/incontrol/details.htm
I’ve been listening to the security now podcast for about 8 years, so my trust of him and yours might vary. The website looks like web 1.0 because it is.

I like people doing challenge runs and speed runs, and occasionally letsgameitout who spends 1000 hours committing to the bit that I might have considered as a passing funny joke. I’d rather watch that then some evening ad riddled free to air.
I’m well over 30, not far from 40. Hobbies can be entertaining like watching someone else race a car. I ain’t gonna be able to do that. But I appreciate those who can.

Gog doesn’t* (as often?) sell licenses that can be revoked as part of purchasing eula and therefore shouldn’t really have to remove the misleading ‘buy’ word.
Many steam games you don’t own and aren’t buying, you’re being granted access that can be revoked by the property owner. That’s not just steam.
*I’m not a big Gog or games purchaser in general so I’m not sure if that’s accurate. I’m sure you get the point though.

This is what I’ve done for years. It just auto starts after OS launch in big picture and I grab my controller. Occasionally I have my wireless keyboard for something but it works fine.
I don’t own a steam deck they’re not available from valve here in Australia. So I’m sure I’m missing out on some polish. But I’ve never seen it so I don’t miss it.
People come over, sit on the couch, grab a controller, steam is loaded, they play game. The OS and then steam is out of the way in a flash. After all I’m after the game not the launcher.

At this point we want antivirus and anticheat out of windows kernel. Microsoft killing access to it will genuinely fix Linux compatibility issues.
It couldn’t be more win-win.
Microsoft is trying to test that approach. The company tested restricting kernel access to third party security vendors in the past, with Vista OS in 2006, but had to backtrack the move.
Symantec and McAfee then claimed Microsoft’s decision to shut off access to the kernel amounts to “anti-competitive behavior.”
Without kernel access, this software may struggle to perform in-depth behavioral analyses of processes and applications, to meet its objectives, said Varkey. “Blocking this access can limit the software’s ability to detect and prevent sophisticated attacks.”
They can’t be trusted, kick out everyone’s access to the kernel. Everyone must use API and that can be interpreted.

Though I agree, you’re trading problems: https://www.forbes.com/2009/05/09/japan-downsize-mizhuho-merger-zombies-tokyo-dispatch.html
The youth can’t get jobs because the positions are filled by entrenched creating this “unless you’re the cream of the crop you won’t get a decent job” permiating from school cumulating into your ranking at education all the way through to graduating in university where only the top cream get reasonable jobs, and many don’t. Even that doesn’t even start to scratch the surface since there’s the aging population, negative population growth requiring less “low skill jobs” like trades in construction…
My point is, I wouldn’t want to replicate that either.

Is that the one where you start with a stealth mission that never appears again in the game? It acts as a mandatory tutorial and makes the whole thing unreplayable because of its heavy handed enforcement? If I’m right, this game is a really good minor evolution of the original for exactly one play through. However I wanted to enjoy it a second time a few times but never got through the intro. Hmm exactly how I’d describe metal gear solid 5. I’ve got great memories just can’t revisit it.

Think of this:
You find a computer from 1990. You take a picture (image) of the 1KB memory chip which is on a RAM stick, there are 4 RAM sticks. You are using a DSLR camera. Your image in RAW comes out at 1GB. You project because there’s 8 chips per stick, and 4 sticks it’ll 32GB to image your 4KB of RAM.
You’ve described nothing about the ram. This measurement is meaningless other than telling you how detailed the imaging process is.

Yep though I’m a sysadmin and can feel for that, these consolidated platforms are being used as a straight “you trust this, when I infect you, I’ll use payloads I’ll temporarily host in github because you adjust already block overseas by default expect a bunch of whitelist trusted domains.”.
It’s technically easy to allow a subdomain, but it’s really hard to unblock just a path.
So yeah, what generally happens is the SOC team complains that the new threat is here, and either vendors (had this with fortinet) move the risk rating of github from a 3.5 to a 6 out of 10, I had put the threshold at a default 5, and now it’s being blocked. I wonder why it wasn’t blocked before, well it wasn’t as risky last week as it is now.
Anyway just thought I’d share the IT sysadmin POV.
More to point, using security as an example, we use SentinelOne and azure sentinel. I’ve had a ‘I want to compare crowdstrike and huntress labs’ because I’ve seen really good things with those xdr seim tools. But I got shot down. Why? We can’t deviate our standards. Well, how will we know if the competition is better? Is our choice good? Who knows.
I still don’t know. I sleep easy knowing it’s not my burden though. It’s their fault if they get compromised on an attack that the other vendor would stop.

Penny drop moment of “oh right we have to look at the competing engines to see our own weakness”? Frankly it should be obvious.
“If you know the enemy and know yourself, you need not fear the result of a hundred battles.”
For me it raises really a odd question about their culture too, since only after inshin’s remaster did they add a policy to review developer tools and technology, in a development company.
I’m trying to not read into it any more than that but I can’t help but imagine there were board meetings beforehand going ‘guys our team want to try using unreal’ and some exec going ‘no it’s banned we only use our own propriety code or else we’ll lose our brand and be washed out! All other engines are banned!’.

To me, not a player, it seems like there’s a long winded explanation/justification for why they uploaded a illegitimately approved run. In Super Mario maker, if you make a level you need to beat it to upload it. They beat it with a tool instead of skill, to ensure the sequence of frame perfect tricks could be completed, something nearly impossible to do by real players.
There were many top level players all at once playing that level non stop. So I feel for them. Training their muscle memory to execute robot timings for what came out to be not a legit level.
Most of what was said was irrelevant, they managed a life story in the middle of an apology.

Although that might be true, the moment the ‘friend’ gave away his account recovery answers to the phisher I think he would have been compromised either way. It was likely that the phisher was in real time actioning a account recovery, and using the friend as the proxy to give answers to the prompts. Plus since it’s already second hand info we can’t tell, but if the phisher simply asked ‘can you read me the code on your authenticator’ or ‘press approve and you’ll complete the recovery process’ and would have been successful.
In investigating account breaches I’ve found most people shamefully don’t retell the whole story they’re embarrassed and upset and fearing loss of employment. They kind of shut down. In this case, social status or opinion could bet harmed so it would be hard to trust the story is complete. Generally my logs come from entra ID and you can see the authentication came from the mobile device even though it was a prompt generated by the phisher.
Anyway I’m a big advocate for layers of security and you’re completely right in your stance. Technology is fragile to exactly what you said. We live in a world of incomplete information using trust and judgement under time pressure and poor sleep. Phishing attacks are ruthlessly designed to target that weakness in people. I’m empathetic when it is successful.

On many systems, the weakest link is that it needs to accommodate a ‘lost my x’ eg mfa, password etc.
Systems often have a way to get in by resetting them by validating through more factors but often weaker ones, “not phishing resistant” factors like security questions. That way the account can get it removed or a new one put on.
Mfa isn’t a silver bullet, it is another layer of Swiss cheese, most people will think twice about giving it away on a chat app. But there’s a reason IT departments sign you up for those phishing simulation and training videos.
But you could still be right in this case, I just wanted to note broadly speaking you can’t assume prefect security is achieved with mfa. You still need to be constantly vigilant.

You’ll make a certain real civil engineer upset by naming it architect and then having a engineer on the front. :)
Nation Engineer gets you away from some of the genetic architect slop (which often follows a successful game) and maybe draws a YouTuber into playing it.
Good luck with your game!