- 0 Posts
- 15 Comments

They will start a dictionary attack on the most common passwords and check their hashes against the stolen database. The speed depends on whether the password hashes obtained are salted in a known method (or not at all). If so, they can perform the dictionary search or brute force locally and VERY quickly.
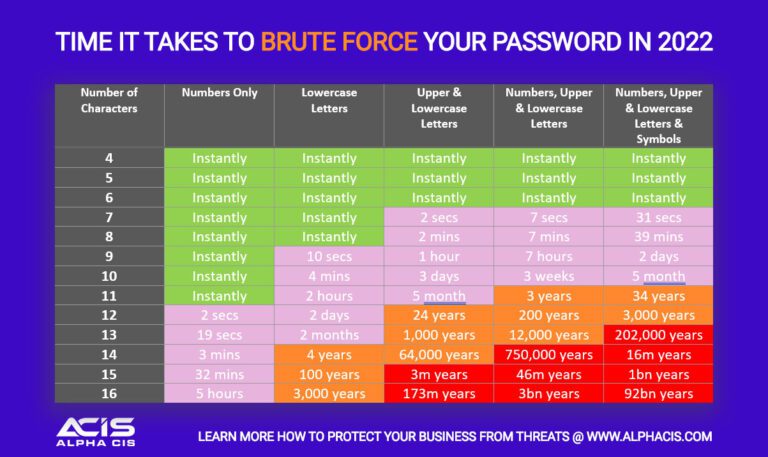
Take these charts with a grain of salt, they always depend on the attacker’s computing power. My password was generated with a password manager and it will take millenia to crack with a reasonable number of modern GPUs so I’ll be able to change it in time.
If the method is not known, they will need to go through the servers, which have rate limits.
The passwords are probably hashed with usernames so they can only attack one person at once but of course, once they have the plaintext password, they can use it anywhere else the user reused it or a variation of it.
I once found a workaround on a trashpicked Android 5.1 phone by Huawei. There was a shitty third-party keyboard during the setup, so I tapped around and found that it has DLC themes. Attempting to download one resulted in a popup “Offline? Check network settings” with a link into the Settings app, where I could set a lock screen passcode and then remove it, which nullified FRP.
Later, I found a YouTube video with instructions for another exploit, which somehow reached Settings via the screenshot shortcut and then attempting to share it via Gmail. I imagine weird phone brands will have several exploits like this.




Look at the app icon